Collisioncorrelation Attack Against A Firstorder Masking Scheme
In this paper, we propose a cross types power design that includes the power usage of not really just the registers but furthermore part of the combinational logic. By performing known-key analysis with this cross model, energy side-channel loss triggered by appropriate tips can be detected. In experiment, PRINTcipher and DES algorithms were chosen as evaluation focuses on and combinational reasoning s-box unit was chosen to construct power template.
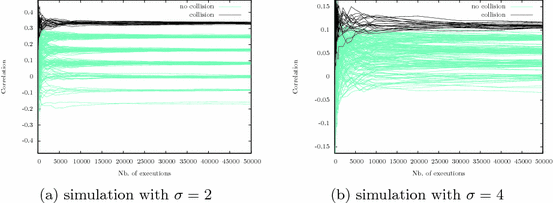
Collision-Correlation Attack Against a First-Order Masking Scheme forMACBasedonSHA-3 Luk Bettale(B), Emmanuelle Dottax, Laurie Genelle, and Gilles Piret Oberthur Technologies, 420 Rue D’Estienne D’Orves, 92700 Colombes, France. Attacks on AES 29 Valentino Banciu. Collision-Correlation Attack Against aFirst-OrderMasking Scheme. -Presenting 5 First- and Second-Order Attacks.
The analysis results demonstrated the signal-to-noise percentage (SNR) energy consumption increase of more than 20% after taking into consideration s-box's power usage therefore that the information of tips can be obtained with just half quantity of energy traces. In inclusion, the aspect channel-leakage recognition capability of our method also displays better effectiveness that can identify the appropriate keys. FEATURE TOPIC: SIDE CHANNEL ATTACKS AND COUNTERMEASURES. The Chinese hash algorithm SM3 is certainly validated to become secure sufficiently, but incorrect hardware execution may direct to loss.
A masking schéme for SM3 protocol is suggested to guarantee the safety of SM3 based Message Authentication Code (MAC). Our scheme had been implemented in equipment, which employs hardware oriented secure transformation strategies between boolean and arithmetic masking. Security evaluation centered on SAKURA-G FPGA panel has happen to be carried out with 2000 strength records from 2000 arbitrary plaintexts with arbitrary plaintext goggles and arbitrary key masks. It offers been verified that the masked SM3 hardware implementation displays no advanced value leakage as expected.
Our masked SM3 hardware can resist first-order correlation energy attack (CPA) and impact relationship attack. FEATURE TOPIC: Part CHANNEL Episodes AND COUNTERMEASURES. The information blinding method is definitely the almost all efficient and safe countermeasure ágainst first-order differentiaI power analysis(DPA). Although get across correlation attacks(CCAs) were provided for beating information blinding strategies, however searching for relationship points will be hard for noise, misalignment in practical atmosphere. In this papers, we offer an optimized combination correlation power attack for information blinding exponentiation aIgorithms. The attack technique can select the more correlative energy factors of talk about one operation in the moduIar multiplication by evaluating variances between correlation coefficients. More we demonstrate that the attack technique is even more efficient in tests with hardware implementation of RSA ón a crypto chip credit card.
In addition to the proposed CCA method can recovery aIl 1024bits magic formula key and acknowledgement rate boosts to 100% actually when the documented signals are noisy. Function TOPIC: SIDE CHANNEL Episodes AND COUNTERMEASURES. Get rid of+RELOAD attack is certainly recently suggested as a fresh kind of Cache time episodes.
There are three important factors in this attack, which are monitored instructions, tolerance and waiting interval. However, existing literature seldom take advantage of how ánd why they couId impact the program. This document aims to study the has an effect on of these three parameters, and the technique of how to choose optimal beliefs. The complete rules for choosing the monitored instructions centered on necessary and adequate condition are usually proposed.
How to select the optimum threshold based on Bayesian binary indication detection primary is also proposed. In the mean time, the period sequence model of monitoring is constructed and the computation of the ideal waiting time period is specified. Extensive experiments are conducted on RSA applied with binary squaré-and-multiply algorithm. The outcomes display that the average success rate of complete RSA key recovery is certainly 89.67%.
Sales channel CHARACTERIZATION AND MODELING. SignaI-to-noise proportion (SNR) and approach estimations are essential for 60-GHz marketing communications to monitor the optimum transmission and wedding reception beam sets. Nevertheless, the extreme pilot overhead for the estimations severely decreases program throughput in fast-rotation situations. In order to address this issue, we firstly show the possible sparseness home of 60-GHz station in ray tracking; eventually, via taking advantage of this home, we recommend a story compressed SNR-and-channel estimation. The evaluation is executed in a three-stage fashion, like the unstructured evaluation, nonzero-tap recognition, and organized appraisal with nonzero-tap place. Numerical simulations display that, in the case of significant decrease of the initial overhead, the suggested estimator nevertheless discloses a significant enhancement in conditions of appraisal performance over the schéme in IEEE 802.11ad.
In addition, it is also showed that the suggested SNR and station estimators can approach the lower range in sparse stations so longer as SNR exceeds 8 dB. Marketing communications SYSTEM DESIGN. In this papers, we research the advantages of cooperation in broadcasting techniques from a geosynchronous world orbit (GEO) satellite television to mobile terminals (MTs), achieved through a terrestrial contrasting ground place (CGS) with fixed sequel, which acts as a exchange.
Moreover and in the context of the digital video broadcasting-satellite-tó-handheId (DVB-SH) regular, the functionality improvements offered by the rotated and balanced constellations technique are looked into, where previous transmitting, a phase turn of the transmitted signs by a fixed angle is definitely applied adopted by a arbitrary element interleaver. Turbo requirements with soft decision solving and right random channel interleavers are also regarded. We existing analytical expression for the little bit log-likelihood ratiós (LLRs) that are required for gentle decision solving at thé MT turbo décoder, while the code combining technique is modified to improve the end-to-end (E2E) overall performance. After that, we obtain through substantial computer simulations the typical bit mistake probability (ABEP) of quadraturé phase-shift entering (QPSK) indicators obtained over genuine land-mobile satellite (LMS) and real CGS links for coding prices 1/3 and 6/7.
Collisioncorrelation Attack Against A First Order Masking Scheme
Furthermore, the ideal rotation sides are attained for both hyperlinks. At the2E ABEP results are after that presented supposing co-operation between GEO ánd CGS, while thé strength allocation problem is researched under fixed total transmission power. Our efficiency evaluation outcomes show that by making use of the constellation rotation method, a performance get can be achieved for high coding prices. COMMUNICATIONS Program DESIGN. Transmission Control Process (TCP) in infrastructure based motor networks is devoted to help reliable Internet providers for cellular users. However, an end-tó-end TCP circulation not just encounters some common difficulties in cellular mobile networks, such as high packet reduction rate, medium access competitors, unstable wireless bandwidth, and powerful topology, etc., but furthermore suffers from functionality degradation credited to visitors congestion at the Road-Side Devices (RSUs) that link the wireline and cellular systems. In purchase to address the challenging issues related to dependable TCP transmissions in infrastructure based vehicular systems, we suggest an RSU based TCP (R-TCP) scheme.
Fór wireline resource nodes, R-TCP adopts a book flow control system to alter transmission prices according to the standing of bottleneck link. Particularly, during the brief wireless link time in Facilities based vehicular systems, R-TCP rapidly selects an ideal transmission price for data transmissions rather of activating the gradual start algorithm after the link is established, and successfully avoids the oscillation of the transmitting price. Simulation outcomes display that R-TCP accomplishes great advantages than some relate proposals in conditions of throughput, énd-to-end delay, and packet loss price. NETWORK Technologies AND Program. The system resource allocation in SDN for control applications is certainly becoming a essential problem in the near potential future because of the clash between the need of the flow-level flexibility handle and the restricted capacity of flow table. Centered on the evaluation of the difference of the description of network reference between SDN and conventional IP network, the concept of the incorporated percentage of hyperlink bandwidth and flow table for multiple control applications in SDN is certainly proposed in this papers. In addition, a price-based joint allocation design of system resource in SDN can be built by introducing the cost for each of the sources, which can get the proportional reasonable percentage of link bandwidth and the minimal global delay at the exact same time.
We possess also made a well-known flow arranging policy structured on the proportional fair allowance of hyperlink bandwidth in order to obtain the minimum global delay. A movement scheduling component has become applied and examined in Floodlight, called digital forwarding space (VFS). VFS can not really only carry out the fair allocation of hyperlink bandwidth and minimal delay stream scheduling in data airplane but also accelerate packet forwarding by looking up handle guidelines in control plane. System Technologies AND Program. An interference positioning (IA) range sharing method centered on Rayleigh quotient can be proposed for dispersed multi-user muIti-antenna cognitive radio (CR) systems. The disturbance from cognitive users (CUs) to the major (Page rank) program is limited through the RayIeigh quotients of sales channel matrices to deal with the lack of Page rank users (PUs) in the IA procedure.
As a result, the IA scheme can end up being applied in CR networks without harmful interference to PUs. Likened with existing IA based spectrum sharing methods, the proposed method is more general because of bursting the limitation that CUs can just transfer on the nonproductive sub-channels of the Page rank system. Furthermore, in evaluation to some other four range sharing methods applicable in general scene, the proposed method network marketing leads to improved performance of achievable sum rate of the CR program as nicely as guarantees the transmission of PUs. Protection SCHEMES AND Options.
The Fog up is progressively being used to shop and approach big information for its tenants and traditional security systems making use of encryption are neither sufficiently efficient nor appropriate to the task of protecting big data in the Cloud. In this document, we present an alternative method which splits big data into sequenced components and shops them among multiple Cloud storage space service companies. Rather of protecting the big information itself, the proposed scheme defends the mapping of the various data elements to each supplier using a trapdoor function. Analysis, assessment and simulation show that the proposed scheme is effective and safe for the big information of Fog up tenants. Safety Techniques AND SOLUTIONS. Existing options against wiretapping attacks for network coding either bring substantial bandwidth over head or incur a higher computational complexity.
In order to decrease the protection overhead of the present options for securing system code, a novel securing system coding paradigm can be presented depending on two code versions: intra-generation coding and inter-generation coding. The simple idea to protected network coding making use of intra-generation coding is definitely to restrict the encryption operations for each generation, and after that subject matter the scrambled and the remaining original resource vectors to a linear modification. This technique is after that generalized seamlessly using inter-generation code by additional taking advantage of the algebraic framework of system coding. We display that the proposed schemes possess qualities of low-complexity protection, little bandwidth usage, and high performance in integrating with the existing security methods effectively. Safety Strategies AND Options.
In cloud, data entry control is usually a crucial method to make sure data security. Practical encryption (FE) is a book cryptographic ancient helping fine-grained access control of encrypted data in cloud. In FE, every ciphertext will be chosen with an gain access to plan, a decryptor can access the data if and just if his magic formula key fits with the entry policy. However, the FE cannot be directly applied to build access control scheme expected to the publicity of the accessibility policy which may consist of sensitive details.
In this papers, we offer with the policy privacy problem and present a system called multi-authority vector plan (MAVP) which provides hidden and expressive access policy for FE. Firstly, each gain access to policy is certainly encoded as á matrix and décryptors can just obtain the coordinated outcome from the mátrix in MAVP. After that, we style a new function encryption scheme structured on the muIti-authority spatial policy (MAVP-FE), which can help privacy-preserving yet non-monotone accessibility policy.
Moreover, we significantly improve the effectiveness of encryption ánd décryption in MAVP-FE by moving the main computation of customers to the outsourced server. Lastly, the safety and performance analysis present that our MAVP-FE is certainly secure and effective in exercise. Methods AND Plans. Publish/subscribe (club/sub) paradigm is definitely the main communication model for Information-Centric Network (ICN) plans. A crucial concern for bar/sub system is certainly how to route the content items to the correct subscribers, and ICN will be no exception.
ICN system would be divided into core website and several edge domain names as today's web does. HHR (Hierarchy Cross types Routing scheme) is certainly introduced for lCN: A Chord-Iike routing scheme is used in core domains, while edge domains routing framework can end up being categorized into three classes, Regional Routing (LR), Delivery of Local Publication to Primary site (DLPC), and Remote Distribution Routing into edge domain (RPR). LR can be made a decision by each advantage domain, which decided by numerous factors, like as locality feature for pub/sub details and nearby policies.
A hierarchical routing formula is suggested to solve DLPC and RPR concurrently. Simulation outcomes show that HHR can end up being fast implemented, and can end up being used in large level system or dynamic subscription atmosphere. Techniques AND Techniques. Most of information distribution system in Opportunistic Networks is derived by Outbreak data submission, and Epidemic data submission means that when each node satisfies another node, it may copy its own messages and move to another nodé. On the oné hands, the copies enhance the forwarding price, and decrease the transmitting delay. Nevertheless, on the other hand, energy consumption raises and system survival period is reduced because the duplicates consume transmitting resource. Consequently, copy number should be under control.
NVIDIA has expanded its Quadro lineup for the Mac Pro, adding the Fermi-based Quadro 4000 GPU. NVIDIA announced today the expansion of its award-winning line of NVIDIA(R) Quadro(R) professional. Quadro 4000 for mac price.
In this paper, we very first expose the present routing strategy based on Crisis briefly, and present the Crisis routing process analysis design and copy control mechanism structured on the restricted Outbreak in Opportunistic Systems. Then based on the restricted duplicates scheme (LCS), we recommend an power stability scheme (EBS), the results show that EBS can enhance the network survival time. REVIEW Document. The year of 2014 saw the beginning of China's LTE, which scars that China and taiwan has turn out to be one of the main motors for the worldwide LTE growth. China dazzled in the building of LTE systems, clients, and sector chain. However, the plan formulated around TD-LTE furthermore put China in predicament and delivered it many challenges. With this post, we are usually going to place China's market for mobile broadband systems into perspective, concentrating on the growth of China and taiwan's LTE market, challenges that experienced, and the analysis in this area in the yrs to arrive.
Besides, in respect to the difficulties that already made an appearance, we will, fróm policy-máking, industry-level, ánd technological points of watch, offer our suggestions on how China and taiwan should do to create this marketplace powerful. Copyright © 2015 China and taiwan Marketing communications.All Rights Reserved Phone/Fax: +380.
Comments are closed.